Blog
Taking the Pain Out of Cloud VPNs: Meraki vMX Delivers!
If you have a Meraki firewall and you’re making a VPN tunnel to Amazon, you no doubt have been thinking (a) Meraki firewalls and the Amazon cloud are awesome and (b) this is a real pain. Only a single tunnel. Failover doesn’t really work. Kludgy workarounds. You’ve got two great pieces of technology, but you haven’t been able to take advantage of all the great native features of the Meraki equipment.
Until now, thanks to Cisco Meraki’s new vMX100 virtual security appliance for AWS.
In short, what virtual MX does is put Meraki’s Auto VPN from its firewall hardware into the Amazon VPC. Auto VPN allows different Meraki security appliances to talk to one another and auto-configure VPN tunnels between themselves. That’s great for VPNs between, say, two office locations. But because there was no Meraki endpoint in the cloud, you were stuck with manual for VPNing and workarounds to get to the cloud.
Consider this very normal situation: You’ve got your firewall set up, and you built a VPN tunnel to your Amazon cloud. You’ve got two ISPs running to your office for the obvious reason that you don’t want to be twiddling your thumbs if Comcast or Verizon has a hiccup. So then say your primary internet connection goes down, and your firewall switches over to the backup, no problem. If you have multiple offices with VPN tunnels running between them, Auto VPN will reconfigure those tunnels no problem too.
But the VPN to the cloud won’t see the new connection, so you’re not able to connect to back-end resources in your AWS environment, unless and until you log in to your AWS console, build a new VPN tunnel, grab the configuration, and change the configuration on the firewall. It’s not a difficult process, but it’s a manual process. Because it requires a human to act, there’s an opportunity for error and a hassle you’ll be going through over and over.
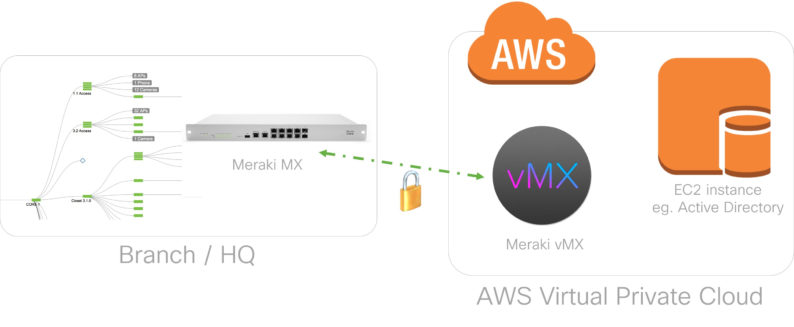
Auto VPN Goes to the Cloud
With vMX100, however, that’s all changed. You can pop an instance in Amazon that’s running basically a virtual stripped-down firewall. Now instead of pointing all of your traffic to the VPN tunnels you would have set up manually between your local environment and your cloud environment, you point it at that virtual appliance and vMX just builds its VPN network with the rest of the Meraki devices in your local environments, extending the Auto VPN to the cloud. So now, if your primary internet connection fails and switches over to the backup, the Auto VPN both locally and in the cloud will see the connection go down, see the secondary is good to go and start advertising itself on that connection instead. All the tunnels will be restored without a single act of human intervention.
As your company grows and you add new physical locations, simply adding a new Meraki security appliance into that location would automatically build VPN tunnels to that location as well. For companies that have a distributed employee base, this not only makes things easier, but it’s also more cost effective.
Get More Out of Your VPN
vMX lets you build fail-over redundancy on the cloud side too. At Mission, for instance, we maintain a backup cloud in a second Amazon region for disaster recovery purposes. Every one of our instances is replicated to our DR site on a nightly basis, so we’re always ready to go if something happens in our primary Amazon region. Without vMX, if we have to switch over to the backup VPC, we have to reconfigure the VPN because the remote endpoint has changed. But with vMX, it’s all automatic: if the main instance goes offline and the backup comes online, the instance in the backup region already has its configuration and it can go build its own auto VPN. No human intervention.
vMX also allows you to extend your use of VPN-level security without having to worry about adding lots of complexity. In addition to the office-level hardware, Meraki also has smaller home networking security appliances that can interface with the vMX virtual appliance. That means you can easily manage VPN-level security for key executives or developers who may be shuttling sensitive information from their homes.
VPC VPN Best Practices & Cost Optimization
Management of all this is really easy too. Meraki’s UI is just a single pane of glass, so you never have to go searching for anything. It’s easy enough that you could walk a total novice through it over the phone, no problem. So you get the automation without added complexity.
Of course, there are design considerations you have to take into account on the cloud side. Consider, for instance, the situation where you have multiple VPCs that you need to integrate to your network. Rather than installing a virtual appliance in each of your VPCs, you can set up a transit VPC that sits in front. The job of that VPC is simply to route all the traffic to, from and between your other VPCs. That transit VPC is responsible for managing all the VPN tunneling to your on-site security appliances.
Cost-wise, vMX requires a license from Meraki and an m4.large instance from AWS. If you have only a couple VPNs, switching from standard AWS VPN tunnels to Meraki vMX on AWS will no doubt add some cost, but you’re also getting the benefits of automatic failover. As the complexity of your system grows and you’d need more standard VPNs, vMX quickly becomes cost-advantageous, especially if you can predict your usage to some extent and utilize the savings of reserved instances.
Bottom line? Meraki vMX100 is a great extension of the Meraki Auto VPN feature, and it stands to make both disaster recovery and routine security management much easier.
Have a question about VPN or other cloud security issues? Drop us a line in the contact form.
Author Spotlight:
Jason Gay
Keep Up To Date With AWS News
Stay up to date with the latest AWS services, latest architecture, cloud-native solutions and more.

